Platform / Identity Threat Detection & Response
Identity Threat Detection and Response
VeriClouds provides a credential-centric solution to stop preventable data breaches. CredVerify APIs work with popular authentication services to block account takeover and credential stuffing attacks that rely on compromised, stolen, or weak credentials.
What is Identity Threat Detection and Response?
Gartner introduced the term “identity threat detection and response” (ITDR) to describe the collection of tools and best practices to defend identity systems as one of the top security and risk management trends to watch for in 2022.
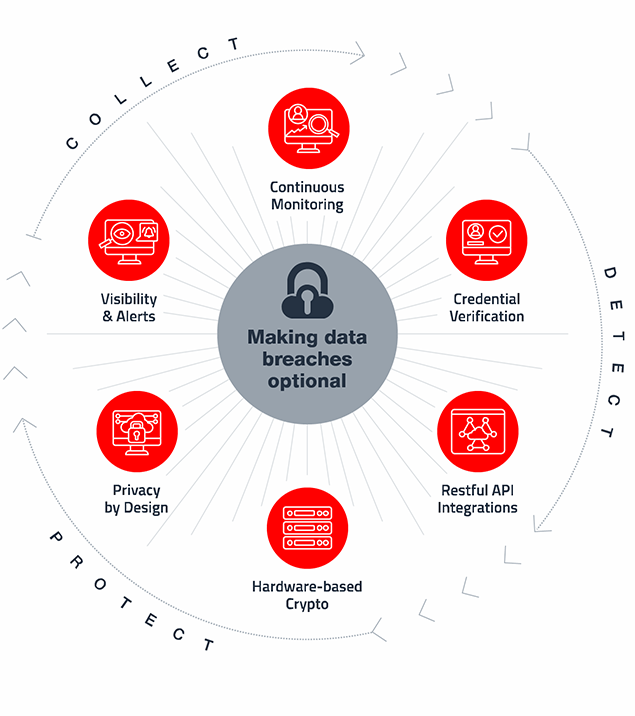
VeriClouds ITDR is a set of modular capabilities that include:
- automated scripts for data collection and secure handling
- data mining and security analytics
- data masking and encryption
- continuous monitoring and notification tools
- integration layer based on restful APIs
- pre-built connectors to leading IAM and security systems
Breach Detection ≠ Identity Threat Protection
It is no longer enough to answer the question, “Has my email been compromised or found in a data breach?” Security and risk management leaders must be engaged with more than breach notification and password blacklists.
Any ITDR platform must be able to answer:
- Are my current passwords leaked or reused?
- How at risk are the executives and privileged users in my organization?
- How do I only notify affected users without forcing a global password reset?
- How can I verify compromised credentials without ever revealing the account identifier or the credential to the service provider?
- Does this user’s leaked credential satisfy or violate my organization’s password policy?
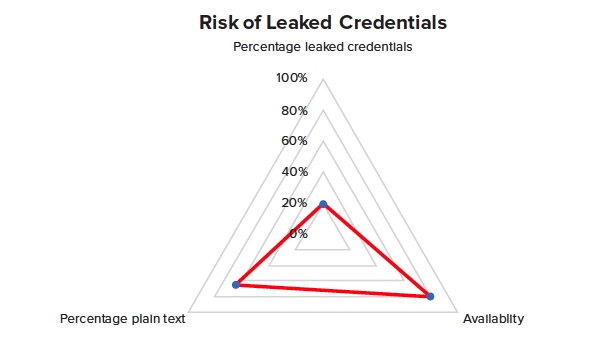
The Growing Risk of Leaked Credentials
Compromised credentials are a rapidly emerging and dangerous risk to organizations that require senior cybersecurity and risk officers within to take notice, assess and sufficiently address. With VeriClouds ITDR, solutions, organizations can have a cloud-scale single pane of glass view of the compromised credentials threat landscape that far exceeds what cyber-criminals and bad actors have available to them.
With VeriClouds-powered credential monitoring and verification, more than 25 billion leaked credentials are secured and checked during login and password changes to enable the automation of risk insight into actionable intelligence, and stop preventable data breaches at the front door.
