Interop with CredVerify Shared Signals Framework
Transmitter for Compromised Credential Signal
In collaboration with VeriClouds, Okta, SailPoint, Cisco, and Helisoft will demonstrate the interoperability of Shared Signal Framework’s Continuous Access Evaluation Protocol (CAEP) at the Gartner IAM Summit in London. For IAM developers, the critical question is how to obtain meaningful security signals efficiently. The essence of Shared Signal lies in disseminating vital security notifications among reliable partners to safeguard users' accounts and digital identities. Our CredVerify SSF transmitter has a real-time credential compromise signal based on billions of stolen credential data from the criminal underground, including the dark web. This is the scale you need to protect your end users and remediate their vulnerability from account takeover. Without data, SSF isn’t effective or practical to protect your end users. We have billions and adding millions more every day.
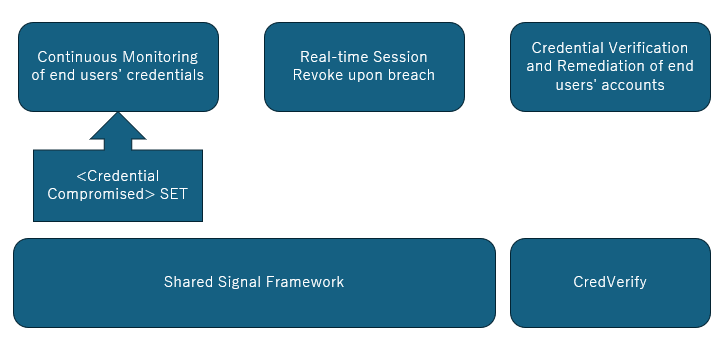
Our SSF Transmitter has three important features that you’ll want with your SSF development
- Session Revoke: If we discover a recent credential compromise of your end user, we can send a real-time Session Revoke Security Event Token (SK-SET) which you can use to revoke the end users’ session, immediately. You can make sure your end user goes through remediation processes by changing passwords or implementing strong multi-factor authentication.
- Credential Compromise SET (CC-SET) is exactly that. The subject has been found compromised. If we issue this CC-SET, you can be 100% sure that end users’ credentials have been found on the criminal underground. Based on this, you may want to send your own
to webapp or to go through a remediation process. - Credential Verification with Passwords. CredVerify Credential Verification technology enables you to check the corresponding passwords of each CAEP subject ID against VeriClouds threat intel data set without dealing with plain text passwords. Our patented encryption technology enables you to make sure that there are no false positives.
The Product Managers should consider these points when planning the implementation of SSF.
- SSF is nothing without the signals, and we have a lot of data. Close to 30 billion stolen credentials and millions added every day. If you have many end users to protect, we can supply meaningful volume to protect with scale.
- Our CredVerify SSF is all about protecting privacy. With our patented Credential Verification technology, you never expose end users’ credentials.
- At the same time, you can be 100% sure the compromise is real with no false positives.


The CISO needs to understand how to stop preventable breaches with CredVerify for SSF
- Account Takeover when the user is already in session but just had his/her credentials compromised at another organization
- Credential Stuffing attacks, when applied at the login
- Lateral breach in single sign-on situations
The Development Leads take advantage VeriClouds resources
- If you are new to SSF, we can supply you with resources such as open-source code for your transmitter.
- Designing remediation policies will be a snap. We know most of the situation where you might need specific remediation process.
- When you develop your SSF receiver, you can interop with our transmitter.

Getting Started with VeriClouds: Next Steps
Contact VeriClouds Shared Signals Framework Consulting Services to learn more. You can learn more about VeriClouds patented CredVerify technology here.
